Problem
You are trying to install third-party libraries via an init script. The init script attempts to download the libraries using curl or wget, but the download fails with an SSL error message.
curl: (35) OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to <hostname>:443Cause
The OpenSSL SSL_connect: SSL_ERROR_SYSCALL error means that your cluster does not have the required SSL certificates to validate the connection to the host.
Solution
You need to install the host's SSL certificate on your cluster.
When the OpenSSL SSL_connect: SSL_ERROR_SYSCALL error occurs you can use curl to debug the issue.
%sh "curl -v <url-that-generates-error>" This option gives you debug output while connecting to the target server. You can check the handshake failure while connecting as well.
Example result
* Trying REDACTED...
* TCP_NODELAY set
* Connected to hostname (REDACTED) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/certs/ca-certificates.crt
CApath: /etc/ssl/certs
} [5 bytes data]
* TLSv1.3 (OUT), TLS handshake, Client hello (1): <---- 1st step in TLS handshake, we do not get to the 2nd
} [512 bytes data]
* OpenSSL SSL_connect: SSL_ERROR_SYSCALL in <hostname>:443
* Closing connection 0
curl: (35) OpenSSL SSL_connect: SSL_ERROR_SYSCALL in connection to <hostname>:443
Get the certificates used by the target server
You can use Google Chrome to export the SSL certificate of the target website.
- Click the Secure button (a padlock) in an address bar.

- Click Certificate (Valid).

- Click Details.

- Click Copy to File….
- Click Next.
- Select Base-64 encoded X.509 (.CER).

- Click Next.
- Save the SSL certificate file as
local-ca.crt. - Click Next.
- Click Finish.
Upload certificate files to your workspace
Save the certificates as workspace files.
Review the Workspace files basic usage (AWS | Azure | GCP) documentation for more information.
Create an init script to install the certificates
Create a new file in your workspace called certificates.sh in the /Shared/ folder.
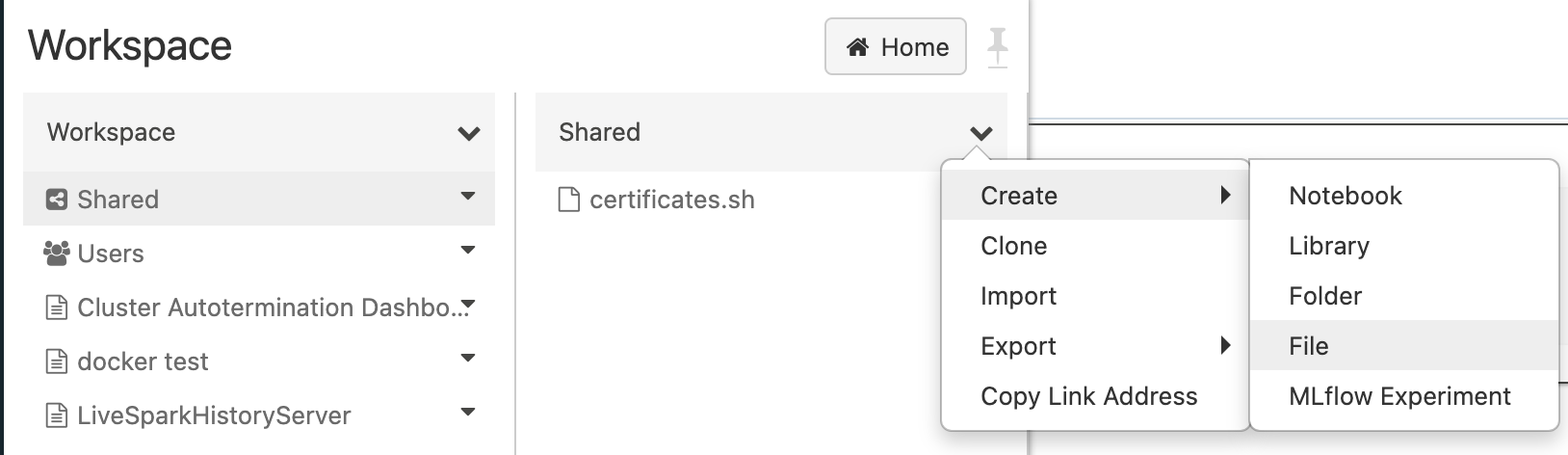
- Click Workspace in the left side menu.
- Click Workspace.
- Right-click Shared.
- Click Create.
- Click File.
- Enter certificates.sh in the text entry field and click Create File.
- Copy-and-paste this init script into the file you just created.
<path-to-cert-file>should be replaced with the path to where you saved thelocal-ca.crtfile in your workspace.
#!/bin/bash
sudo apt-get install -y ca-certificates
sudo cp <path-to-cert-file>/local-ca.crt /usr/local/share/ca-certificates
sudo update-ca-certificates
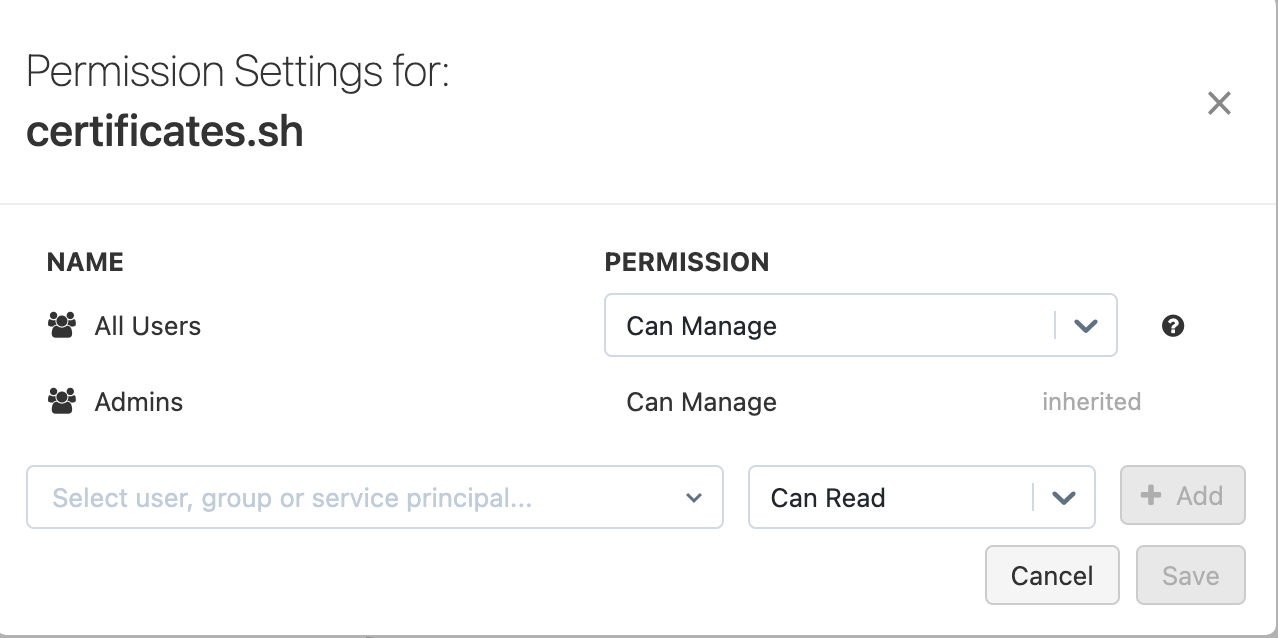
Verify init script permissions
Check the permissions for certificates.sh and make sure all users who are creating clusters have the can_run and can_read permissions. The creator of the file and administrators have all permissions by default.
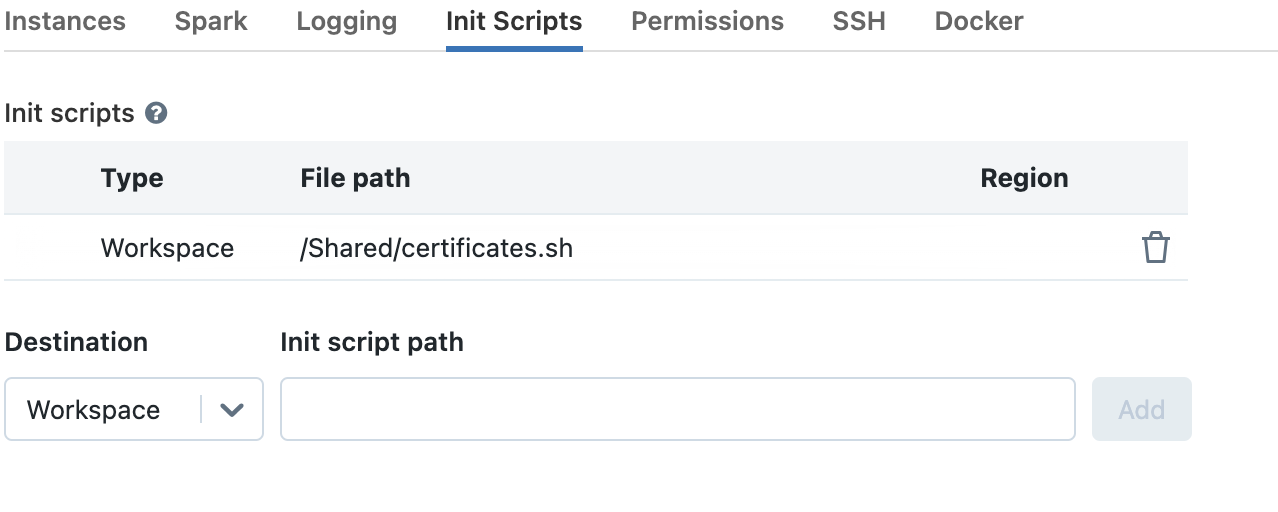
Configure a cluster-scoped init script
Follow the Use cluster-scoped init scripts (AWS | Azure | GCP) documentation to configure certificates.sh as a cluster-scoped init script.
Info
The certificates.sh init script should run before the init script that generated the OpenSSL SSL_connect: SSL_ERROR_SYSCALL error message.
Restart the cluster
Restart the cluster and verify that your init scripts successfully complete.
For more information on the certificate store, review the Ubuntu CA trust store documentation.