IP access lists can be used to restrict access to Databricks based on known network locations. Once enabled, an IP access list requires uses to login from an allowed address. If a user attempts to login from any IP address not on the access list, the login is denied. Review the IP access list documentation for more details.
Best practices involve periodically reviewing the IP access logs to see if any login attempts were made from outside the permitted range. After you identify access attempts made from prohibited IP addresses, you can follow up with appropriate action. For example, if the attempts were made by a legitimate use, you may want to permit additional IP ranges in the access list. If the attempts were not made by legitimate users, you may want to review your security profile.
Instructions
Information on access attempts is stored in the Databricks audit logs. You can use Databricks notebooks to analyze the audit logs and track activities performed by users. This example shows you how to search the audit logs for times when someone tried to login to your workspace from a prohibited IP address.
- Load the audit logs as a DataFrame and register the DataFrame as a temp table. You will need to enter the S3 <bucket-name> and the full <path-to-audit-logs>. Review the Configure audit log delivery documentation for more information.
%scala val df = spark.read.format("json").load("s3a://<bucket-name>/<path-to-audit-logs>") df.createOrReplaceTempView("audit_logs") - Query the audit log based on the date range and accounts that attempted access from a prohibited IP address. You will need to enter the <start-date> and the <end-date>of the date range to search before running the sample code.
%sql select date, eventTime, orgId, sourceIPAddress, actionName, userAgent, get_json_object(rawMessage, '$.response.statusCode') StatusCode, get_json_object(rawMessage, '$.response.errorMessage') AS errorMessage from audit_logs where date >= "<start-date>" #Date in yyyy-MM-dd format and date <= "<end-date>" #Date in yyyy-MM-dd format and serviceName = "accounts" and actionName = "IpAccessDenied" order by eventTime - The results display all instances when a user was denied access based on their IP address.
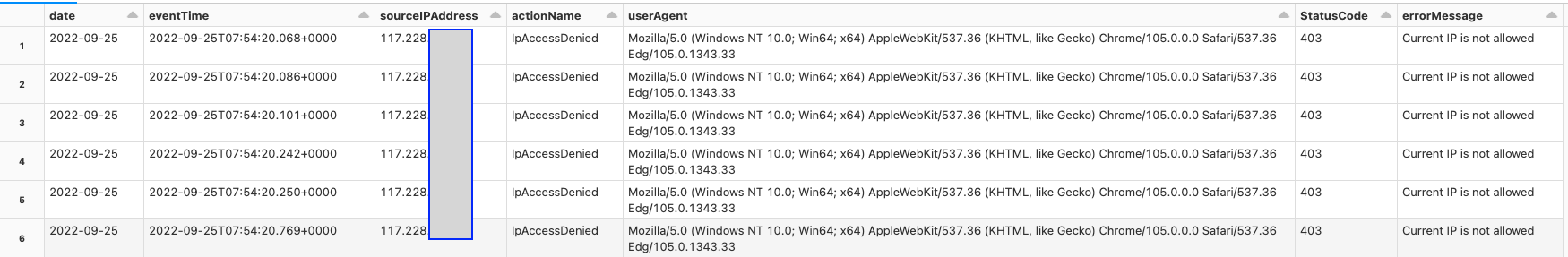
- Take appropriate action based on the results and you use case.